What is Phishing?

What is Phishing?
Phishing is a type of cyber attack where malicious actors impersonate legitimate entities to deceive individuals into providing sensitive information, such as usernames, passwords, credit card details, or other personal data. This information is then used to commit fraud or gain unauthorized access to systems and accounts. The term "phishing" is derived from the analogy of "fishing," where attackers use bait (deceptive messages) to lure victims into a trap.
How Phishing Works
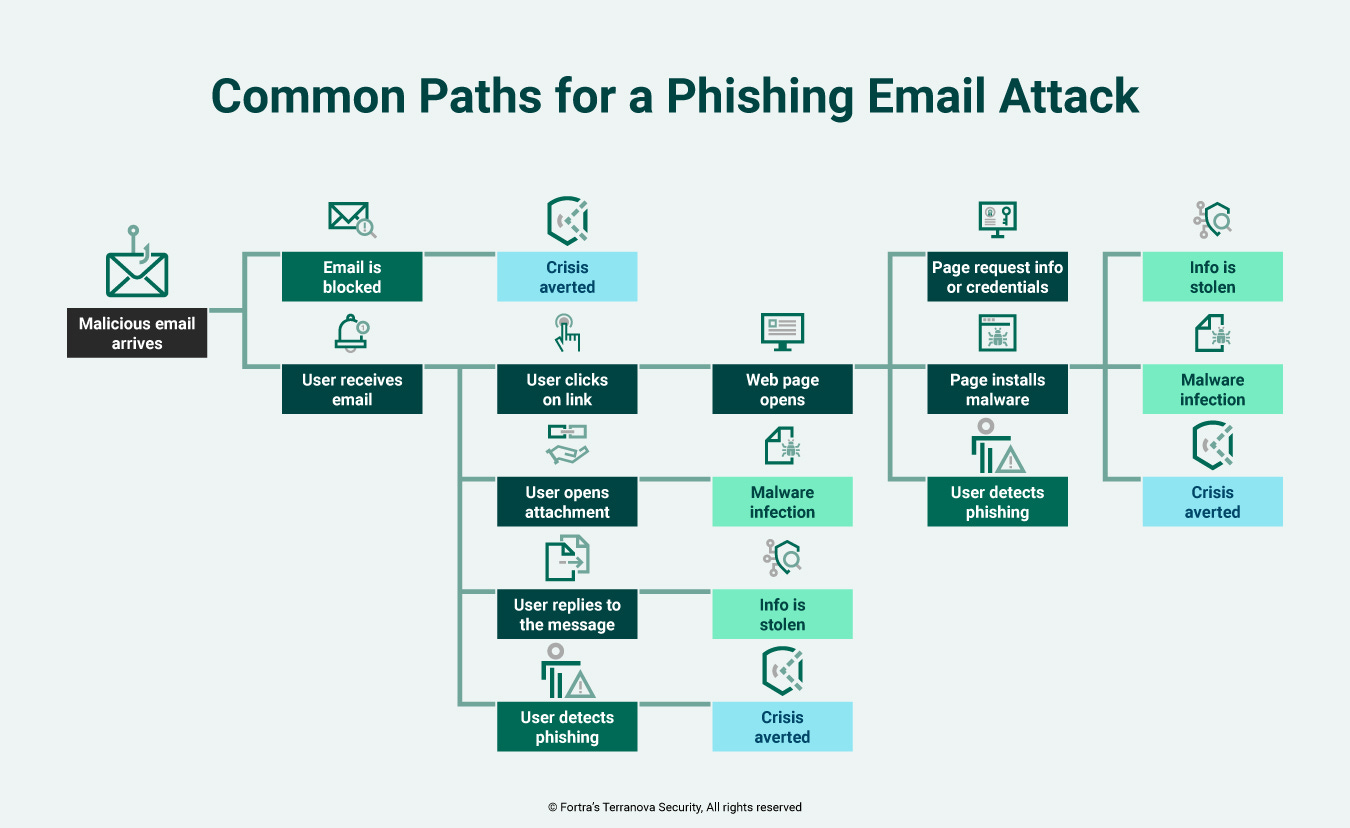
Phishing attacks typically involve the following steps:
Preparation: Attackers create a convincing message or website that appears to come from a trusted source, such as a bank, social media platform, or well-known company.
Distribution: The malicious message is sent out to potential victims via email, text message, social media, or other communication channels.
Deception: The message often contains urgent or enticing language to trick the recipient into taking immediate action, such as clicking a link or downloading an attachment.
Exploitation: Once the victim takes the bait, they are redirected to a fake website or prompted to enter sensitive information, which is then captured by the attackers.
Common Types of Phishing
Email Phishing: The most common form of phishing, where attackers send emails that appear to be from reputable sources. These emails often contain links to fake websites or malicious attachments.
Spear Phishing: A more targeted form of phishing, where attackers customize their messages to specific individuals or organizations, often using personal information to make the attack more convincing.
Whaling: A type of spear phishing that targets high-profile individuals, such as executives or public figures, with the intent of gaining access to sensitive organizational information.
Smishing: Phishing attacks conducted via SMS text messages, often including links to fraudulent websites or prompts to call a phone number controlled by the attacker.
Vishing: Phishing conducted through voice calls, where attackers impersonate legitimate organizations to trick victims into providing personal information over the phone.
Recognizing Phishing Attempts
Check the Sender: Verify the sender's email address or phone number. Be cautious if the address looks suspicious or unfamiliar.
Look for Generic Greetings: Phishing messages often use generic greetings like "Dear Customer" instead of your name.
Beware of Urgency: Be skeptical of messages that create a sense of urgency or demand immediate action.
Check for Errors: Look for spelling and grammatical errors, which are common in phishing attempts.
Verify Links: Hover over links to see the actual URL before clicking. Legitimate sites will have consistent and recognizable domain names.
How to Protect Yourself
Educate Yourself and Others: Awareness and education are the first lines of defense against phishing. Regular training can help you and your team recognize phishing attempts.
Use Security Software: Install and update anti-virus and anti-malware software to help detect and prevent phishing attacks.
Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring additional verification beyond just a password.
Monitor Accounts: Regularly check your accounts for suspicious activity and report any unauthorized transactions immediately.
Be Skeptical: Always question unsolicited messages that ask for personal information or prompt you to click on a link.
Conclusion
Phishing remains one of the most prevalent and effective methods used by cybercriminals to steal sensitive information. By understanding how phishing works, recognizing common signs of phishing attempts, and implementing robust security practices, individuals and organizations can significantly reduce their risk of falling victim to these attacks. Stay vigilant and always verify before you trust.